
How Ransomware Locks Files on Google Drive
By Andrew BurtonRansomware is often considered to be an on-premises technology threat. A user downloads a suspicious file or clicks on a sketchy link, and ransomware locks files on their computer. If they’re logged into a local network, files on additional computers and shared drives may be impacted as well. People don’t realize that it doesn’t necessarily stop there, and your SaaS apps are far from immune. Ransomware can spread to G Suite data, particularly if you use the Google Drive sync capability.
Google Drive sync allows users to automatically synchronize some or all of their local files with Google Drive copies. Users can work on files offline, and when they reconnect to the Internet, changes are automatically synced. This is obviously convenient, especially when using Drive to collaborate with others, but it can also be a security vulnerability.
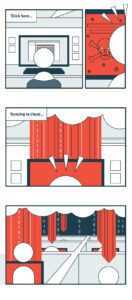
Here’s why: If files on a computer are infected by ransomware, they will sync to Google Drive and corruption will exist on both versions. And, if you are using Google Drive to collaborate with colleagues, ransomware can spread rapidly across all shared files and folders—creating a much larger issue. In a Google Drive Help Forum post a Google Products expert said:
“Encrypted ransomware files will sync back to the Google Drive server. You may be able to restore the files to a previous version but unfortunately, there isn’t much of a solution besides this. Best of luck to you!”
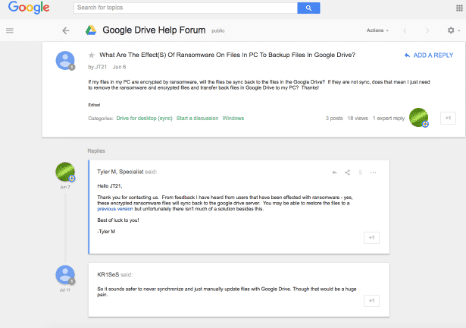
Best of luck? Ouch, that stings a bit, no?
However, you can avoid ransomware with a proper SaaS backup solution such as Backupify for G Suite. With Backupify, your Google Mail, Drive, Calendar, Contacts, and Sites data is automatically backed up to the secure Datto Cloud three times a day. This independent copy allows you to restore data to a point in time before your files were encrypted.
The recent WannaCry attack has shown exactly how vulnerable businesses are to ransomware, so now is a good time to put a strategy in place. To protect your business data, ensure your software is up-to-date and patched, use reputable antivirus software, use a backup solution that automatically takes frequent backups of your data, and educate end users on what to watch out for (suspicious attachments, links, etc).